Is RCS Messaging Secure?
Unmasking the Security Challenges of Rich Communication Services
RCS messaging is on the cusp of becoming the go-to messaging format across all smartphones with its wealth of engagement-boosting benefits. It’s an exciting time for CPaaS providers and brands, but with great opportunity comes great responsibility. Before diving head first into the content-rich world of RCS, there is one thing we must consider, and if you’re familiar with Enea’s expertise in messaging security, you probably know where we’re going with this.
Security First, RCS Enrichment Second
Rich Communication Services bring fantastic opportunities for both CPaaS providers and brands in the form of RCS Business Messaging (RBM). RBM enables brands to enhance their B2C communications and explore new realms of customer experience. But there is a caveat – security must come first. Messaging threats are still present on RCS, they just look a little different.
Firstly, let’s take a look at the RBM delivery chain to identify who will be impacted by the security challenges that come with RCS Business Messaging:
Who should care about RBM Security?
1. The Sending Brand
If customers are receiving fraudulent RBM messages under the guise of a trusted brand, they may lose faith in sending brands, causing reputational damage and potential customer churn.
2. The CPaaS Provider or Aggregator
If a CPaaS provider is a source of spam and scam RBM messages, they risk being disconnected from operator networks. The security responsibilities of CPaaS providers and aggregators are set to expand with RCS Business Messaging – but more on that later.
3. The RBM provider (e.g. Google Jibe)
With RCS Business Messaging, the RBM provider authenticates senders to verify that they are legitimate (though this is not a failsafe security solution). Securing the channel is important for RBM providers to maintain trust and relationships with partners in the delivery chain, and ensure the long term viability of RBM as a channel.
4. The Mobile Network Operator (MNO)
MNOs need to keep subscriber inboxes clean from spam, fraud and abuse to preserve subscriber trust and comply with regulation.
5. The Subscriber
The security of RBM messaging directly impacts mobile users. If messages aren’t protected, their inboxes may be inundated with spam and unsolicited or inappropriate messages. They could suffer losses to scams. This leads to customer complaints and endangers trust in the brand, the mobile network, and RBM.
What Attacks are Happening over RCS?
A Shiny New Attack Surface for Scammers
For sending brands, RCS Business Messaging offers new avenues for engaging customers with compelling content. Brands can incorporate images and videos in their messages, and derive valuable insight and action from their customers through conversational messages. Unfortunately, these use cases are also available to bad actors.
One thing we know about scammers is that they are creative – and RCS offers new canvases to play with:
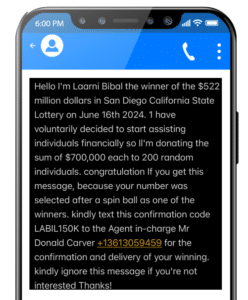
1. Group Chat Scams
With SMS, we see scammers spoofing short codes to appear as a legitimate brand or organization, like your local bank or post office. RCS Group Chats offer scammers a new spin on spoofing. A familiar example of this kind of fraud is a WhatsApp group chat scam. Fraudsters can create and name group chats after legitimate organizations, even adding a couple of dummy users to lull the user into a false sense of security. With some social engineering, the scammer encourages victims to pay up under the guise of fake crypto investments, false job offers, or fabricated competitions.
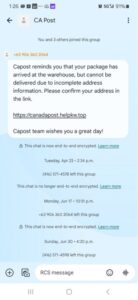
RCS Group Chat used to send scam messages
2. Conversational Spam
RCS introduces the possibility of interactive conversations between brands and consumers in RBM. Unfortunately, scammers like to use conversation to engage with potential victims. In a technique known as conversational pig butchering, attackers use innocuous messages like “do I know you?” to start a conversation with an intended victim. From there, they use conversation to build trust, potentially moving to other channels to continue the scam. It’s a slow burner for scammers, but it’s effective, especially with chatbots being used to send conversational messages at scale.
3. Hiding URLs in Plain Sight
Bad actors want to hide URLs to bypass messaging firewall filters. Enea has uncovered numerous URL-disguising techniques over the years, including through the use of cloud storage and Google services. These techniques continue to evolve in RCS messaging. Some tricks we’ve seen so far include:
- Hiding URLs in images to avoid detection by spam filters.
- Asking the user to search up terms in the message.
- Hiding the URL between brackets or other characters, and instructing the recipient to remove them in search to activate the URL.
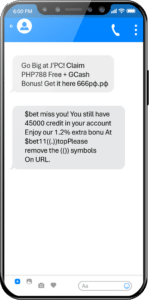
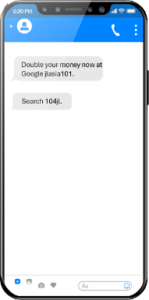
Examples of RCS messages containing hidden URLs – can you spot the technique they are using?
4. A Picture Worth a Thousand Words
Rich media is a great tool for engagement, allowing brands to include fun visual elements in their communications. However, we have come across a number of cases of images being used to hide malicious content in plain sight, including price listings for illicit goods, advertisements for illegal weapons, even entire phishing messages to avoid firewall detection. The importance of image inspection in the new age of rich media messaging cannot be underestimated. Images need to be screened to assess whether it is appropriate for a particular recipient, situation, or location. For CPaaS providers, being a source of malicious or inappropriate content could result in being restricted by operators.
Scammer inserts the scam message into an image to avoid detection
5. Grey Route Fraud
Grey routes don’t disappear in RCS messaging. Group chat functionality, for example, is being leveraged for grey route fraud. Bad actors set up group chats and name them after legitimate organizations, like Microsoft in the example below. They then use the group chat to send grey route messages. Since the group chat is named after a legitimate brand, it doesn’t appear suspicious and goes undetected. RCS Grey routes hurt message monetization and absorb revenues, posing a financial threat to the messaging ecosystem if they are not addressed.
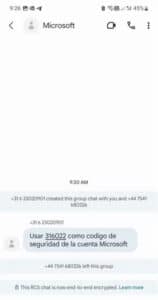
Example of an RCS Group chat being used as a grey route
Offensive AI and Rich Media – A Perfect Spam Storm
The latest addition to the attacker tool kit, Offensive Artificial Intelligence enables attackers to work smarter, faster, and at scale.
Bad actors sweep public domains for personal details like first names, phone numbers, and zip codes. Using AI, they create highly personalised scam campaigns with messages that grab attention and increase the likelihood of a response. With the help of AI, scammers produce these campaigns in multiple languages, enabling them to send localised and personalised messages on an even bigger scale. Add to this the enhanced engagement features of rich media like buttons, images, and embedded links, and we’ve got a dangerous combination that is helping attackers cast a wider net for victims.
Encryption is a Double-Edged Sword for Messaging Security
End–to–end encryption is a security mechanism intended to prevent messages between the sender and receiver from being intercepted. The message is encrypted at the sender’s device, and decrypted at the receiver end, preventing messages from being intercepted and read. Sounds great, right? There’s a catch. While encryption addresses some of the security issues we see with SMS, it provides a gateway for other attacks.
Encryption of RCS Messages Gives Rise to New Modes of Attack
In a bid to bypass encryption, bad actors are finding ways to infiltrate mobile devices. Once attackers gain access to a handset, they can leverage that device’s connection to others to send malicious messages. If the message originates from a (seemingly) legitimate sender, encryption becomes meaningless – there is no way to determine whether that sender has bad intentions or not. What’s more, if users perceive encryption as complete security, they’re not questioning whether a message could be a scam. This blind trust may be leading mobile subscribers into attackers’ open arms.
Since RCS has come to the fore, Enea’s threat intelligence experts have seen spikes in attack vectors like mobile malware and SIM banks being used to gain access to handsets as a point of entry for attacks. These attacks are already happening, and will continue to increase as RCS adoption rises.
Encryption Means Shifting Responsibilities for RBM Security
Traditionally, the mobile network operator is responsible for ensuring messages are not a threat to subscribers, but encryption means they don’t have the visibility to inspect RCS messages for fraudulent content. So where does that leave us?
In the eyes of regulators, since mobile operators provide the service that enables messages to be sent and received, they are responsible for ensuring that service is safe and secure. However, with RBM messages being encrypted from the point of origin, CPaaS providers and aggregators are likely to have a bigger role to play in securing them.
When it comes to P2P RCS messaging, spam reporting is going to be a really important tool going forward. Since encryption limits visibility, spam reports from subscribers will be an important source of intelligence on the messaging threats that are out there. Gathering and sharing this information could help us stay ahead of messaging fraud, but this will require a mindset shift from the industry. We need to start opening up conversations around the value in sharing this kind of intelligence, and how it can be leveraged to better secure RCS channels. This is important for RCS Business Messaging as well. It’s imperative that we keep subscriber inboxes clean from spam to establish and maintain that precious trust in RBM and the messaging ecosystem.
Key Takeaways for CPaaS Providers and the Mobile Ecosystem
In many ways RCS is a safer channel than SMS, but it is not without security challenges. Bad actors are taking full advantage of offensive AI capabilities, combining them with rich media features to create scams that are more engaging, persuasive, and personalised than ever before. We need to be prepare for that by using AI defensively to counter the threat.
End-to-end encryption helps to keep communications private and prevents them from being intercepted along the way, but it is not synonymous with security. Encryption also limits visibility into messaging threats, hindering operators’ ability to conduct security checks and limiting intelligence on current and emerging forms of messaging abuse. Due to this restricted visibility, CPaaS providers and aggregators will be required to take on more responsibility for RBM security.
Enea’s RBM handbook “Securing Business Messaging in the Age of Rich Media” is a guide for CPaaS providers on the essential steps to build a secure RBM environment and protect user trust. Get your copy here>
Want to learn more? Watch Simeon Coney’s presentation on this topic at the MEF Leadership Forum Barcelona.