RBM Handbook for CPaaS – Chapter 1
Why Messaging Must Start with SMS, MMS and RBM
The rise of A2P messaging has benefited brands and created significant revenue for mobile network operators, messaging aggregators and CPaaS providers in the last 15-20 years. However, the growth has also caused security challenges, as rogue elements have been drawn to the messaging ecosystem, targeting consumers as well as the ecosystem itself.
As RCS adoption grows and becomes ubiquitous across mobile devices, RCS Business Messaging (RBM) will play an increasingly important role in the communication between brands and their consumers. But its success hinges on maintaining trust, which depends on robust security measures to prevent fraud, spam and misuse. While RBM offers several security advantages over SMS, many threats from the SMS era remain relevant today. Additionally, the rich media landscape introduces new vulnerabilities that must be addressed.
Handbook: Securing Messaging in the New Age of Rich Media
This is an excerpt from our handbook Securing Messaging in the New Age of Rich Media, a guide to RBM security for CPaaS providers. Download the full handbook for a comprehensive overview of RBM security.

What sets SMS, MMS, and RBM Channels Apart?
Misuse is not unique to SMS or RBM. Any messaging channel with enough users, including proprietary direct messaging apps (such as WhatsApp, Viber, iMessage, Signal, and Line), is exposed to spammers and fraudsters. However, RBM, MMS, and SMS are unique in the messaging space because they are public telecom standards independently implemented by hundreds of mobile network operators and supported by an ecosystem of numerous companies of varying sizes. This sets them apart from other channels. From a security perspective, there are two key reasons for CPaaS providers to ensure these telecom services are the first of their communication channels to be secured: regulations and visibility.
Operators will be Holding CPaaS Accountable for RBM Security
A significant difference between telecom services, such as A2P SMS and RBM, and proprietary communication services is that telecom services are defined through standards owned by the telecom industry (e.g., ITU, GSMA) with the involvement of most mobile network operators. Because of the ownership of these standards, operators will be held responsible and accountable by regulators, irrespective of whom actually provides and delivers the majority of the service. Operators have a far closer relationship with regulators than any of the proprietary service providers. Therefore, it is anticipated and reasonable to assume that regulators will consider RCS and RBM services under the operator’s control. This is not the only reason why regulators will pay more attention to operators and native telecom services than to proprietary services. Other reasons include:
1. Protecting Critical Infrastructure
Mobile networks are considered critical infrastructure. National security requires them to be kept robust and secure. They must also be able to function during crises and allow subscribers to trust information sent over the network.
2. Ensuring Economic Stability
Mobile networks play an instrumental role in the economy. Regulations ensure that they operate efficiently and contribute to economic growth and stability. If consumers don’t use mobile communications because of spam and misinformation issues, it will negatively affect the economy.
3. Compliance with International Standards
Mobile networks are based on international standards, and compliance with these standards is essential for interconnectivity, roaming, technology evolution etc. This requires coordination from a security perspective.
4. Consumer Protection
Mobile networks are, by necessity, national entities since they need spectrum, which is nationally allocated. This makes it easier for NRAs to regulate MNOs rather than international direct messaging services. Since mobile operators already fall under regulatory scrutiny, consumer protection also becomes part of the regulators’ mandate.
5. Regulatory Pressure
While It’s in the best interests of proprietary service providers to secure their own channels, since their user base is their key asset, regulators play the role of security enforcers in the telecom ecosystem.
From a regulatory standpoint, RBM (and RCS) are not different from SMS or MMS. All three are telecom services terminated in mobile networks, and involve messages being sent to a phone number. This is a foundation for regulators, and their mandate to regulate that operators must protect subscribers against unwanted communication in all these channels. Regulators will not allow operators to neglect their responsibility to keep subscribers safe only because they outsource some of their infrastructure. Therefore, these messaging channels still fall under regulators’ mandate requiring operators to protect subscribers from unwanted communication. While operators will still be held responsible for keeping subscribers safe, CPaaS providers will have a very important role to play in securing these channels.
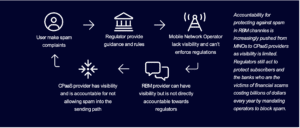
CPaaS Responsibilities Increase as RBM Becomes the Standard A2P Messaging Channel
While MNOs have pushed regulatory responsibilities for A2P traffic upstream to aggregators and CPaaS providers in the past, they have also maintained control over SMS and MMS traffic terminated in their networks and have been able to filter out unwanted messages to protect subscribers. This changes with RBM. Unless an MNO runs its own RCS infrastructure, the MNO will be virtually blind to the content of RCS and RBM messages as it will pass through the network as pure IP traffic regardless of whether it is encrypted or not. However, regulators still hold them accountable for the content delivered through their networks, which means they will require clean traffic from CPaaS providers.
CPaaS must Comply with Messaging as a Platform (MaaP) Sending Policies
The fact that Messaging as a Platform (MaaP) services like Google Jibe filter messages for spam does not relieve MNOs from their obligations, or CPaaS from responsibilities. Instead, CPaaS providers must comply with the MaaP’s sending policy and ensure all messages are acceptable and appropriate. CPaaS providers must demonstrate their ability to manage content securely and ensure that all RBM messages adhere to regulatory standards and operator policies, thereby supporting MNOs in fulfilling their regulatory obligations. Violations against the policies will result in retribution, such as sending restrictions, suspension from terminating traffic in the network, or fines.
Spam Reports will be Increasingly Valuable for MNOs
An important information channel for MNOs is spam complaints collected through spam report features in messaging apps or services such as 7726 reporting. Regulatory authorities also keep track of spam complaints from subscribers, providing further input to MNOs.
Like what you’ve read? Click below to get your free copy of Enea’s RBM Handbook for CPaaS providers – Securing Messaging in the Age of Rich Media and Artificial Intelligence.