Think Before You Google: Unmasking Malicious URLs
For many of us, Google is a cherished side-kick, answering our burning questions in just a few clicks. Due to the widely used and recognizable Google brand, it makes sense that mobile subscribers are less suspicious of URLs containing the brand name “google.com”.
This kind of trust is being exploited by malicious actors trying to trick mobile subscribers by hiding behind seemingly legitimate URLs. Attacker techniques can include luring subscribers to their websites under false pretenses, and stealing sensitive information such as credit card details, email or social media credentials, and other personal data.
Recently, a spam campaign using this technique, which we call the “CBD scam”, was identified by our threat intelligence team. The spam campaign involves the use of a legitimate Google address, “google.com/amp”, with the spammer using encoded characters to conceal the rest of the spam URL.
Anatomy of the Scam
This type of URL, beginning with “google.com/amp”, is known as a Google Accelerated Mobile Page (AMP) Viewer. It is specific to Google, in that it enables users to access pages through Google’s infrastructure with optimal speed and performance. AMP is an open-source initiative, which allows web developers to create web pages that load quickly and efficiently on mobile devices. In this case, the scammer is using this feature to modify the appearance of a malicious URL.
Modifying the URL this way is simple, requiring limited technical knowledge, and helps the scammer to achieve a couple of objectives:
1.Bypass Firewalls
Since the URL the scammer is using contains the domain name ‘Google’, it gives the message a better chance of bypassing firewalls and spam filters, which detect and block messages with URLs containing spam domain names.
2. Earn the subscriber’s trust
Mobile subscribers recognize the Google brand, and therefore may be more likely to believe a link containing the brand name is legitimate.
Some examples observed by Enea’s threat intelligence team:
At first glance, these messages may appear to be well-meaning health care suggestions found through a Google search. Mobile subscribers would need to thoroughly examine the complete URL path to avoid falling victim to such scams.
If we look closely at this example:
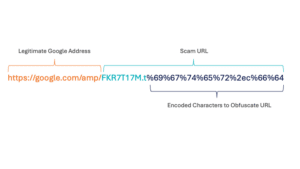
It is partially a legitimate Google address, and part scam URL with encoded characters to obfuscate the scam URL. While the visible URL is:
The actual URL is:
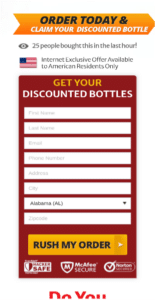
Once clicked, the URL leads the subscriber to the following landing page, claiming to sell CBD gummies. In reality, this website is not genuine and is designed to trick people into sharing their credit card details with online scammers.

Scam web page claiming to sell CBD gummies
Some of the follow up pages, asking the user to input their credit card details:

Unmasking the URL
As threat intelligence experts, we help to identify threats like these targeting an operator’s subscribers. In cases where we detect a suspicious URL, we typically examine the number of redirects and the layers of intermediate pages that a link traverses before reaching its landing page. One click of this link involves the following redirects:
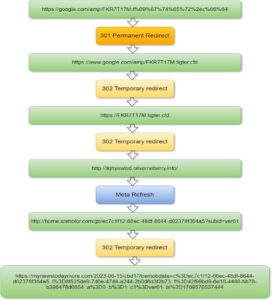
Terminology breakdown:
1. Permanent Redirect: Permanently redirects the URL to a new location (webpage), indicating that the original URL has been permanently moved to a new address.
2. Temporary Redirect: Temporarily redirects the URL to a new location (webpage), indicating that the original URL is temporarily moved or unavailable, and future requests should continue to use the original URL.
3. Meta refresh: The html meta tag is used to direct browsers to automatically refresh the page or redirect to a different URL after a specified time.
In this case, one of the redirects of the scanned URL does not utilize standard redirect methods to navigate to other locations. Instead, it employs the ‘meta refresh tag’ in its source code to direct to the targeted spam URL. This approach typically remains undetected by a regular firewall’s scanning methods.
Additionally:
- The purpose of the text body of the message is analysed against the intention of the website.
- We use URL decoding methods to review the actual URLs and specific rules to handle these situations.
What can we learn from this?
Scammers are becoming more sophisticated, experimenting with different methods to exploit the “trust factor” associated with well-known and reputable sources, websites, or links. As regular users of major online platforms, mobile subscribers often trust URLs related to these platforms, which is a common mistake. Mobile users must exercise caution when being asked to click a link, even when it looks legitimate, to avoid falling victim to SMS phishing attacks.
On the operator side, deploying a combination of threat intelligence and a messaging firewall is the best way to dynamically react to threats in good time, keeping your subscribers safe and maintaining their trust in your network. Enea’s messaging firewall combined with our messaging threat intelligence helps operators detect and respond to SMS threats like this one quickly, preventing the message from reaching the subscriber. By ensuring mobile subscribers are not inundated with spam and scam messages, Enea helps operators to keep their customers satisfied and secure. Read more here>.






