Take Two: Selfmite.b Hits the Road
In the end of June we reported about a new SMS worm dubbed Selfmite. Fortunately the number of infections at the time was not large due to the fast actions that we took including a notification to Google on the malicious goo.gl URL used by the worm. The worm used a legal advertising platform and pay-per-install for monetisation which is described in our blog entry about the first version of the Selfmite SMS worm. However in the last few days we have discovered and have been tracking a new version of this worm. Selfmite is back and it has some serious improvements.
Description and statistics
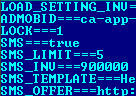
Selfmite.b is still an SMS worm with similar functionality but different approach. Its code is injected to a trojanised version of the legitimate Google Plus app which appears after the malware installation. This is different from the original version of Selfmite. Second, Selfmite.b uses configuration file which is downloaded by the worm from hxxp://209.190.28.50/setting.php which contains SMS spam message, the URL and other data used by the worm:
Selfmite.b configuration file
The worm uses one of the following SMS texts:
Hi buddy, try this, its amazing u know.http://x.co/5****
Hey, try it, its very fine.http://x.co/5****
If you read the description of the first version of Selfmite worm you will notice that it was designed to send an SMS message with the link to itself to the first 20 contacts in an address book. The second version of Selfmite goes a lot further and sends one of the messages above to all the contacts. In a loop. This means that potential victims will continue to receive malicious SMS message from an infected phone until either the operator detects and blocks these messages or an owner of an infected phone removes the malware. According to our data, Selfmite.b is responsible for sending over 150k sent messages during past 10 days from a bit more than 100 infected devices. Plus, this time Selfmite.b victims can be found all other the globe, infected phones can be found in 16 countries: Canada, China, Costa Rica, Ghana, India, Iraq, Jamaica, Mexico, Morocco, Puerto Rico, Russia, Sudan, Syria, USA, Venezuela, Vietnam. To put this into perspective that is over a hundred times more traffic generated by Selfmite.b compared to Selfmite.a.
We notified Go Daddy about the malicious x.co URLs and at the moment both shortened URLs have been deactivated. But the fact that the author(s) of the worm can change it remotely using a configuration file makes it harder to stop the whole infection process.
What does this all mean? First, it means nothing good to any victim of the Selfmite.b worm. As well as spamming all their contacts, any owner of an infected phone can face huge bills due to a large number of SMS messages being sent by the worm. Besides that, huge amounts of traffic from a single phone can affect the operator’s network and may lead to blocking of the phone number for spamming.
Monetisation
Selfmite.b has some improvements in this area as well. The first version of this SMS worm used Mobogenie application installation and pay-per-install scheme. This time authors decided to track the victims IP address to cause different results depending on a user’s origin.
The malware uses two different ways of monetising the infection.
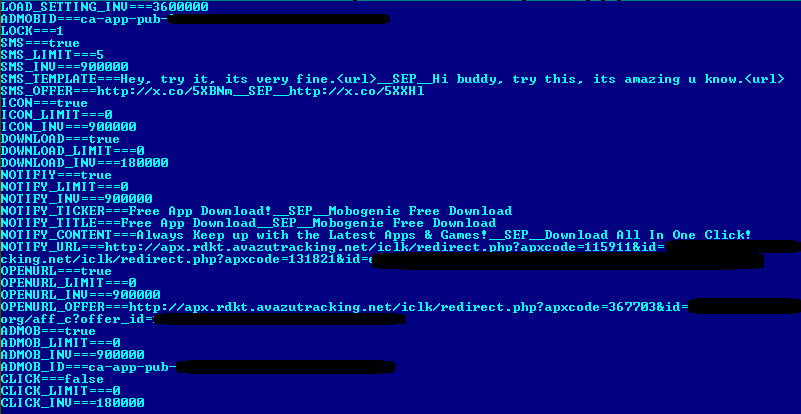
The first way is when the worm creates icons with similar names on a desktop pointing to 2 different URLs. The icon names and URLs are obtained from the following file hosted on the C&C: hxxp://209.190.28.50/icon.php
File icon.php used by Selfmite.b
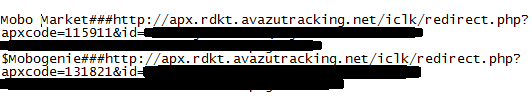
Selfmite.b creates the following icons on a mobile desktop:
Icons created by Selfmite.b
If user clicks on one of the icons the following content he receives depends on his country of origin. E.g. if a user is from Ireland he will be redirected to the following premium subscription page:
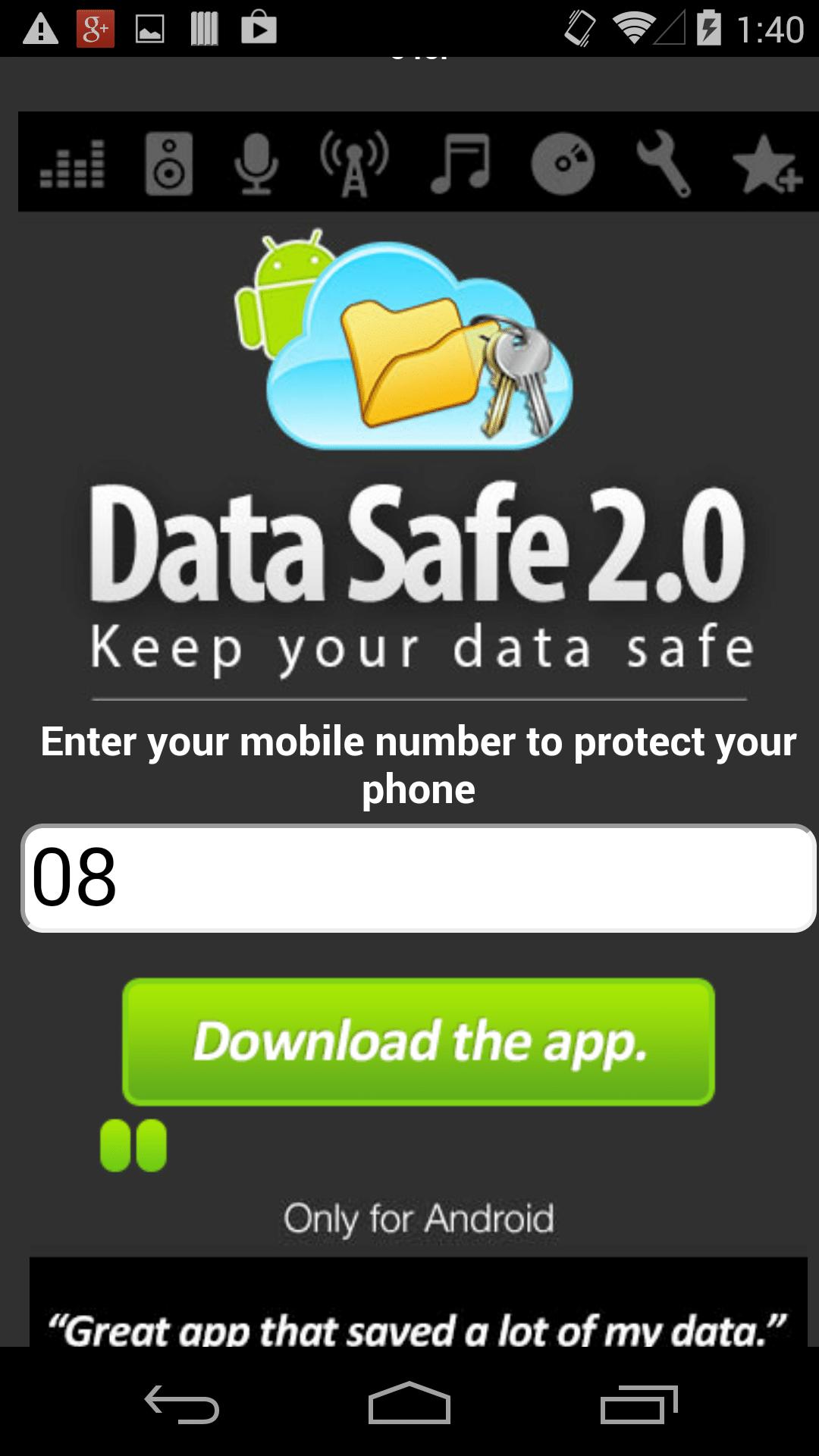
Geo-targeted premium subscription page
E.g. in case of Russian IP address an automatic download of Mobogenie app (as it happened in case of the first version of Selfmite worm) will start.
The second way of monetisation is when Selfmite.b uses the trojanised Google Plus app. First, when the user clicks on this app it tries to point to a certain app in Google Play (depends on a current configuration file). Second, when the user exits Google Play an unsolicited subscription website opens in a browser on the phone. In both cases the malware author(s) use advertising and referral networks to monetise this behaviour.
The content of the subscription page may vary:

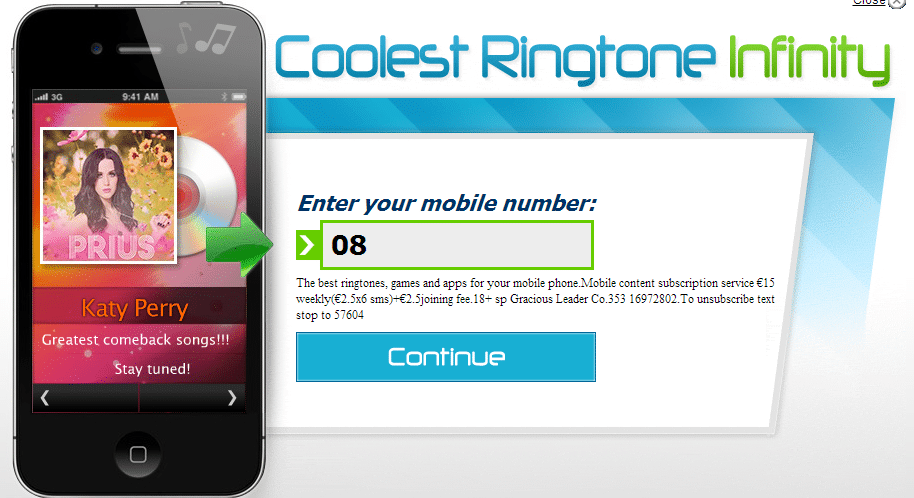
Various versions of subscription pages
Conclusion
It looks like that this new version is like ‘Selfmite worm on Steroids’. It has a far more aggressive self-propagating mechanism and therefore has a bigger number of victims. Plus it’s many ways of monetisaton together makes Selfmite.b a really serious issue. We continue to monitor the situation and will keep you posted with any updates.
googleplus.apk MD5: 1bf7a3639bf81e2260547fe5e04f864c
Thanks to Yicheng Zhou and Cathal Mc Daid for contribution.
P. S. What happens if a spam message has been received by an iOS user? After clicking on the one of the malicious shortened URLs user will be redirected to the fitness app in Apple’s App Store: