Four Pragmatic Ways AI is Already Improving Zero Trust Network Access
Zero Trust Network Access is a conceptual framework for cybersecurity that is relatively young but already widely adopted, and many ZTNA solutions are already demonstrating impressive maturity in their effective use of machine learning (ML) and artificial intelligence (AI) to boost ZTNA performance. To understand how, let’s look first at the basic ZTNA paradigm.
ZTNA is a conceptual framework that assumes every user and device should be considered untrustworthy until proven otherwise, and once vetted, should be granted only least-privileged access to the precise resource needed, and nothing else. And even that limited trust can be revoked at any sign of suspicious behavior.
It is a model that is rapidly displacing the legacy castle-and-moat model of cybersecurity, in which known and trusted users are allowed to move freely about the castle grounds once they’ve passed through the main gate, and for a very pragmatic reason: there are hardly any castles left. There has been a massive migration of users, data and applications outside the corporate perimeter – and they’re not coming back.
And what are the core ZTNA functions required to secure today’s diverse, distributed, and dynamic networks? They are:
- Thoroughly vetting each user (a person or a thing) at each connection with multi-factor authentication and contextual data,
- Using micro-segmentation and hidden IP addresses to ensure the user can only access (and see) the specific resource they need,
- Continuously monitoring network segments for any sign of misplaced trust or external intrusions,
- Taking appropriate action to address any threat that arises.
Research into solution vendor deployments of ZTNA (1) shows that the four most prominent ways AI/ML is being used today is to enhance critical subfunctions within each of one of the above core functions. Specifically, these subfunctions are:
- AI-enhanced user authentication
- AI-enhanced micro-segmentation
- AI-enhanced threat detection
- AI-enhanced alert response
Let’s look at each of these and how they improve the core ZTNA functions.
AI-enhanced user profiling
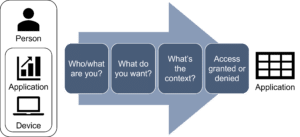
ZTNA uses a context-based, multi-factor authentication system that evaluates:
- A person and their multi-source identity verification,
- A device and its security profile, and
- An application and its risk level.
Leading vendors are using AI to enhance this process by analyzing large volumes of behavioral data extracted using network visibility tools like DPI, and creating baseline models of what is normal and abnormal behavior in order to automate the assignment of risk levels and appropriate authentication processes for each connection request.
AI/ML is further being applied to incorporate biometric data in authentication processes, such as the way a user holds their device, the way they walk, or how they type. It can also incorporate more familiar AI/ML-basedbiometric identification like face, voice, fingerprint, and iris recognition (with the caveat that methods are combined to build in protection from future AI-driven spoofing of such data).
AI-enhanced micro-segmentation
The use of micro-segmentation to enforce least-privileged access is a key tool in ZTNA to prevent lateral movement. However, because the number of users and applications can be in the thousands for many organizations, automation is a must for developing and enforcing micro-segmentation policies and controls. AI is ideally suited to this type of security operations automation task, and especially valuable given cybersecurity staffing challenges and the laborious nature of micro-segmentation tasks in complex environments. Accordingly, this has been one of the earliest ZTNA tasks to be enhanced with AI. And as with behavioral modeling in authentication processes, AI-enhanced micro-segmentation is built using DPI-based traffic flow analysis with a high level of protocol and application recognition.
AI-enhanced threat detection
In ZTNA, once a connection request has been authorized, network segments are continuously monitored to ensure the (limited) trust granted to a user has been well-placed, and to detect any intrusions by outside actors. Such network-based intrusion detection is especially important in contemporary environments where perimeters – and the traditional defenses that go with them – are few and far between.
To deliver this important protection, ZTNA vendors are using AI/ML-based threat detection that analyzes traffic patterns and behaviors in real time in combination with ML and non-ML-based DPI traffic visibility tools like session correlation, port-based classification, deep file inspection, protocol anomalies and more. In advanced DPI engines, such tools can help identify potential threats like an evasive use of complex tunneling, file spoofing, domain fronting, the use of covert communication channels, unauthorized VPNs, anonymizers, potential MiTM attacks and more.
AI-enhanced alert response
Finally, when a threat is detected, action needs to be taken. This includes applying predetermined rules (like terminating connections) for clearly defined and clearly identifiable threat types, as well as analyzing alerts and determining appropriate defensive measures for potential threats that require analysis.
Here, innovative ZTNA providers are using AI to improve and automate alert analysis and response processes. This is particularly valuable given lean staffs and ever-escalating alert volumes.With DPI-powered alert contextualization and interactive, AI-powered alert analysis tools and recommendation engines, SOC staff working in AI-enhanced ZTNA environments feel more empowered, are less stressed, and achieve far better results than peers working in non-AI enhanced environments.
Realizing the promise of ZTNA through AI
Zero-trust architectures are designed to meet the agility, scalability and security needs of today’s dynamic, distributed digital ecosystems. They are also intended to improve the user experience over legacy VPN architectures, with a consistent process whether they or the resource they are accessing are on or off the corporate network. AI-enhanced ZTNA tools and processes, built on a foundation of accurate and reliable network traffic intelligence, are already helping to deliver on these promises today, and the AI journey in cybersecurity has only just begun.
1. Findings based on internal research by Enea of deployments by ZTNA vendors who embed Enea’s deep packet inspection (DPI) engine in their solutions.
Click here for more information on how accurate, detailed traffic and application insights delivered by Enea’s Next-Gen DPI can raise the effectiveness of ZTNA solutions.
This article was first published on The Fast Mode.
Next-Gen Deep Packet Inspection (DPI) Technologies for Artificial Intelligence (AI) Success
For more on how to boost the quality and differentiation of AI-based networking and cybersecurity products with unique, high-quality data, and compute efficiency:





