Always be wary of messages, emails and calls from numbers you don’t recognise that are saying they’re someone you know or a major organisation, and asking you to do something urgently.
What Happens If You Take the Bait?
SMS Phishing Attack Explained
Have you ever received a text message claiming to be from a financial institution informing you of a fraudulent transaction on your account, urging you to call a number, or access a page through a link? You are not alone. Fraudulent text messages are on the rise, with over 3.5 billion mobile users receiving spam texts on a daily basis. In this blog, we explain the intricacies of this type of social engineering attack.
The Flaw in Our Phone System
How Your Phone Could Be Tracked Without Your Knowledge
Have you ever watched someone’s phone being hacked in a spy movie, and thought it might be a little far-fetched? Then this might come as a surprise to you. In a practical experiment, Derek Muller shows how your phone can be compromised without your knowledge – by hacking into his friend’s phone remotely. Find out how mobile phones can be weaponised for location tracking, call interception and more in this video by Veritasium.

AI Messaging Threats
How AI Empowers Cyber Scammers
With the rise of rich media content, AI-driven messaging threats are becoming a growing challenge across the messaging ecosystem. To combat malicious AI, advanced defensive AI technologies are essential. The ongoing battle between offensive and defensive AI highlights the importance of agility, flexibility, and innovation in the industry’s approach to messaging security. Learn more about how messaging scammers are using AI to their advantage in an excerpt from our handbook on rich media messaging security.

The AI Shield
Using Artificial Intelligence to Stop Cyber Threats
Just as attackers are turning to AI, defenders are doing the same. AI can help detect threats faster, spot unusual behavior, and stop attacks before they happen. In this blog, we explore how AI is becoming a shield for organizations and individuals alike — and why observability and speed are crucial in staying one step ahead.

Think Before You Google
Unmasking Malicious URLs
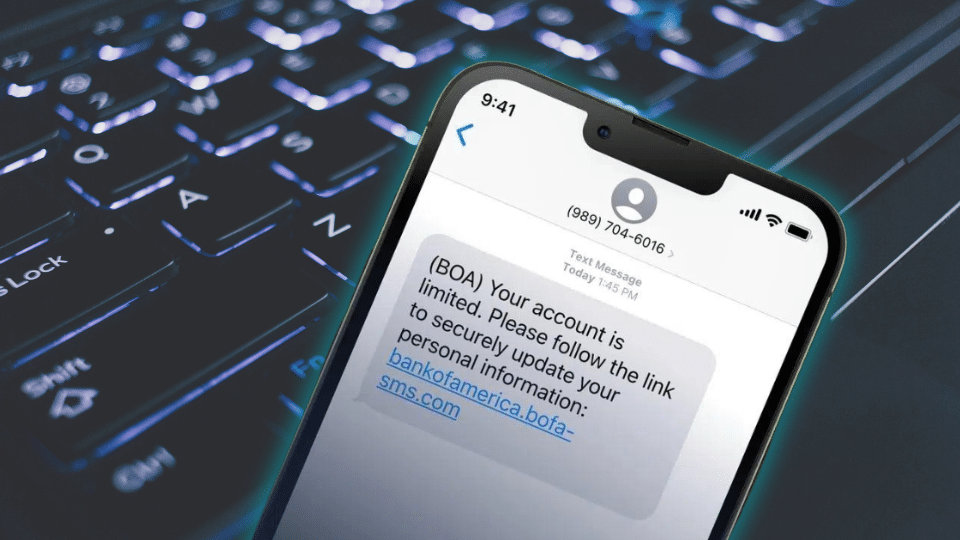
For many of us, Google is a cherished side-kick, answering our burning questions in just a few clicks. We recognize and trust the brand. Unfortunately, this trust is being exploited by malicious actors trying to trick mobile mobile users by hiding behind seemingly legitimate URLs. The spam campaign involves the use of a legitimate Google address, with the spammer using a special technique to conceal the rest of the malicious URL.

Scam Alert
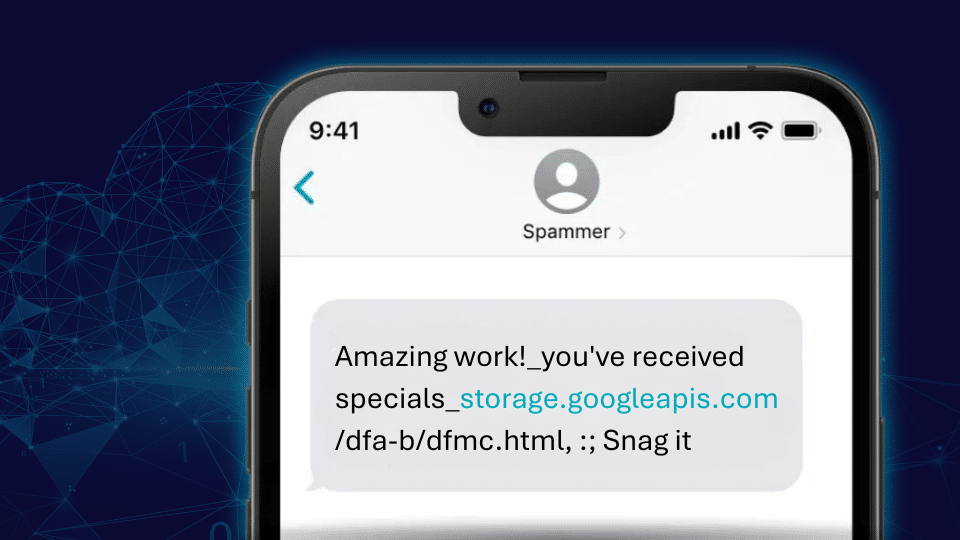
Exploiting the Cloud: How SMS Scammers are using Amazon, Google and IBM Cloud Services to Steal Customer Data
This year, Enea’s Threat Intelligence Unit uncovered campaigns that exploit cloud storage services like Amazon S3, Google Cloud Storage, Backblaze B2, and IBM Cloud Object Storage. Threat actors are using these storage platforms to redirect users to malicious websites, with the ultimate objective of stealing their information. It all starts with a phishing text message.
telecom is critical infrastructure
Software Compliance with EU Cyber Resilience Act
The EU’s NIS2 made telecom critical infrastructure. Now the Cyber Resilience Act is coming—holding organizations accountable if the software they use hasn’t been checked for weaknesses, both at deployment and over time.
Take the recent vMuse airport check-in disruption: under the new rules, airports themselves could be liable, not just the software provider. Cyber resilience is now business critical in the EU.

Security in Internet of Things
Why Enterprise VPNs Are So Important but Challenging for IoT CSPs
In IoT, security and scale must go hand in hand. Enterprise VPNs with Private APNs are essential for protecting sensitive IoT traffic—but traditional setups are manual, slow, and don’t scale across thousands or millions of devices.
Enea IoT CCS changes that. With Multitenancy Private APN, CSPs can automate Enterprise VPNs, split traffic securely, and let enterprises set them up in minutes.
Read More

Cybersecurity News Stories
Want to discover more cybersecurity insights from Enea? Browse our recommendations:
Data Charging Bypass
Protect Your Revenue & Stop Zero-Rating Fraud
Protect your revenue with our updated white paper for Mobile Network Operators. Fraudsters are exploiting zero-rating policies, bypassing data charging rules, and draining operator profits. Learn how to detect and block these threats with fresh insights from Enea.

Protecting children online
Parents & Network Safeguards
As part of Cybersecurity Month we are highlighting the UK’s Online Safety Act, which became law about one year ago. Recent reports from Ofcom on children’s attitudes to media and its use show the complex nature of online safety. Did you know that nine in ten children own a mobile phone by the time they reach the age of eleven in the UK? Creating a safer environment for children to access the complex online landscape requires attention from both content providers and communication service providers.