RBM Handbook for CPaaS – Chapter 3
Verified Senders, Encryption and Rich Media: Improving Messaging but Adding New Risks
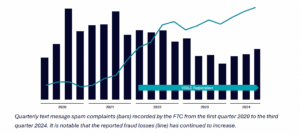
One of the threats to user experience over SMS is the lack of fundamental security mechanisms. SMS messages are susceptible to spoofing, fraud, and spam. The lack of encryption threatens privacy and discourages users from using SMS to send content perceived to be sensitive or confidential. One of the driving forces behind adopting RBM is overcoming these flaws, providing a better customer experience, and preserving a high level of trust. However, while sender verification and encryption are highly appreciated by consumers and add significant value to RBM, they are also features that can be misused for malicious purposes unless adequately protected.
Handbook: Securing Messaging in the New Age of Rich Media
This is an excerpt from our handbook Securing Messaging in the New Age of Rich Media, a guide to RBM security for CPaaS providers. Download the full handbook for a comprehensive overview of RBM security.

Why Sender Verification and Encryption Aren’t Enough
SMS spoofing has been a significant issue for many businesses that have seen their brands hijacked by scammers. RBM introduces brand verification to ensure that the brand whose logo and name you see is, in fact, the sender. While sender verification is a critical feature that will help consumers identify trustworthy messages and help brands regain trust, it is not a foolproof method. If spammers manage to impersonate legitimate brands, the verified business checkmark, logo, or replicate the brand in some other way, it could give message recipients a false sense of security.
Vetting Processes do not Guarantee Compliant Messaging
Vetting and “Know Your Customer” (KYC) requirements have previously been used to curb unsolicited communications. When 10-digit long codes were introduced as an alternative to short codes for business messaging in the US, it came with a vetting process and KYC requirements for CPaaS providers. However, data indicates it has not profoundly impacted messaging spam. There might be several reasons for this:
- Consumers that are not aware they have opted in.
- Content drifting. Consumers receive communication they did not expect or want from a business they accepted other types of communication from (e.g., receiving marketing messages when expecting notifications only).
- Lack of awareness or human errors causing inappropriate content or content not suitable for a specific audience to be sent.
- Rogue elements get vetted under false premises and then send spam under the protection of the vetting approval, i.e., intentional abuse of the A2P channel.
- Account hijacking. Brands may have their accounts and/or agents hijacked by spammers.
- Rogue downstream players. When messages are sent through a chain of aggregators before terminating in a mobile network, a downstream player may inject spam.
Challenges With Large Scale Vetting
It is crucial to understand that while the vetting process for RBM senders is designed to enhance security and trust, it cannot guarantee the complete exclusion of fraudulent senders from the ecosystem. The sheer volume of potential senders alone poses a significant challenge (there are between 300 and 400 million businesses worldwide). While the exact number of businesses that use messaging for customer communications is difficult to pin down, some estimates point to more than 50%. That would be the equivalent of up to 200 million businesses. But even if only a few percent use messaging, that is still potentially 10s of millions of businesses.
With millions of businesses potentially adopting RBM in the coming years, thoroughly vetting each business becomes a monumental task. It will be impossible to “Know Your Customer” well enough. The current customer identification and due diligence process is partially manual and time-consuming. This creates a bottleneck that could lead to cursory checks or prolonged wait times, potentially allowing rogue elements to slip through by misrepresenting themselves or impersonating other brands.
Spammers can also bypass vetting using other methods:
- Rogue senders may create false business profiles that closely mimic legitimate brands. Using names, logos, and colors that mimic those of a well-known brand can cause anyone to mistakenly identify the sender as that particular brand. Business information could be falsified or altered for the vetting process, leading to approval despite breaching the launch criteria.
- Spammers can hijack an agent. For example, access to the brand’s account and its agents can be obtained through phishing attacks.
Moreover, the dynamic nature of business operations and the ever-evolving tactics of fraudsters present ongoing challenges. A business that passes the initial vetting process may later engage in fraudulent activities, exploiting their approved status. The current vetting system lacks continuous monitoring mechanisms to detect such shifts in behavior. Additionally, the decentralized nature of the vetting process, with different operators and aggregators potentially having varying standards and resources for verification, creates inconsistencies that fraudsters can exploit.
The Janus Face of Encryption
The second significant change in RCS and RBM is encryption. SMS has been criticized for lacking end-to-end encryption, which could potentially expose personal data and violate privacy. Without encryption, messages also risk being intercepted or manipulated in transit.
While P2P RCS messages can be end-to-end encrypted under the right circumstances, the same is not possible for RBM. Encryption is not yet part of the Universal Profile (the RCS and RBM standard). RBM content can be encrypted in transit at the transport layer, but this still leaves openings for manipulation and interception between hops. This also means that the message content is unprotected on the user’s device and, hence, susceptible to manipulation by malware. On an infected device, URLs and reply actions in messages can be replaced with malicious ones, or sophisticated malware can use the content to craft responses in the name of the unknowing user. The metadata is not encrypted, which has implications for privacy and fraud. Metadata can, for example, reveal a lot about a user’s communication habits, such as who they are communicating with, when, and how often. This information can be exploited for targeted advertising, surveillance, or even blackmail. Another way spammers can exploit metadata is to identify active phone numbers and target them with malicious messages, for example by injecting messages directly into an existing conversation.
Another factor to consider is that operators may choose to block encryption for incoming RBM messages. Regulatory pressure is a potential driver for this, as some operators might be forced to filter and inspect content and messages to fulfill regulatory requirements. The monetization of grey route traffic could also provide an incentive for operators to block encryption and enable traffic inspection.
How Encryption Protects Spam
When present, encryption protects the privacy and integrity of all messages, both legitimate and spam. For spammers, encryption can provide a protected pipeline to reach subscribers without risking detection or blocking. For SMS and MMS, MNOs can inspect A2P messages terminated in their networks, providing a critical control point in the ecosystem, but in normal circumstances, RBM message content is encrypted between the RBM provider and the handset. When this is the case, the MNOs lose the ability to exercise control and filter traffic. Without executing this control, the message paths through MNOs become freeways for spam.
The stage at which encryption is applied matters, and will influence what kind of protection is required to keep the channel clean. When it comes to RBM, the ability to filter content at the point where messages first enter the messaging path will be essential.
Like what you’ve read? Click below to get your free copy of Enea’s RBM Handbook for CPaaS providers – Securing Messaging in the Age of Rich Media and Artificial Intelligence.