The Future of Deep Packet Inspection: Key Findings from the Enea DPI Survey
Major changes are underway in the telecommunication and security industries that are generating new needs in traffic visibility and require a new approach to network traffic analysis.
As a supplier of DPI-based traffic intelligence, we wanted to better understand how DPI is used, the challenges facing solution vendors and their customers, and how DPI technology needs to evolve to continue to deliver traffic visibility that meets the needs of the telecommunication, cybersecurity and enterprise markets going forward.
So we reached out to OEM product managers who are navigating these changes from the front lines* and asked them to participate in a DPI survey. The responses have yielded valuable insights into current operations and roadmaps, but also reveal much more than specific details about DPI requirements. They confirm that telecom and security vendors and their customers are confronting rapid changes as the cloud transformation, 5G networking, work from home practices, encryption, and the Internet of Things (IoT) have a profound effect on network users, devices, and services. They need traffic recognition tools to adapt to these new needs, and to deliver important insights about network traffic even without inspecting the main content (or payload) of packets.
Key findings
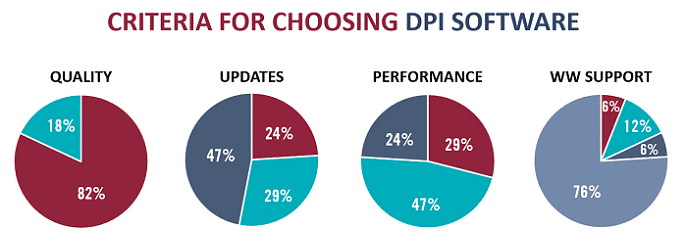
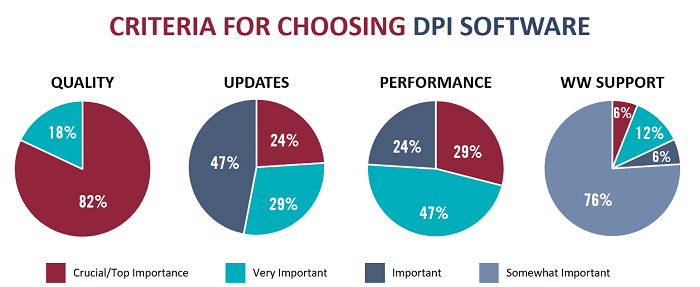
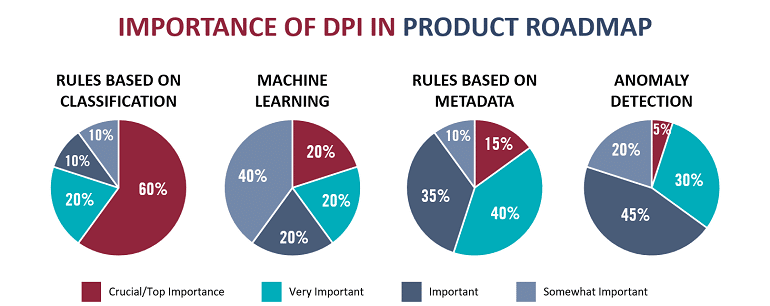
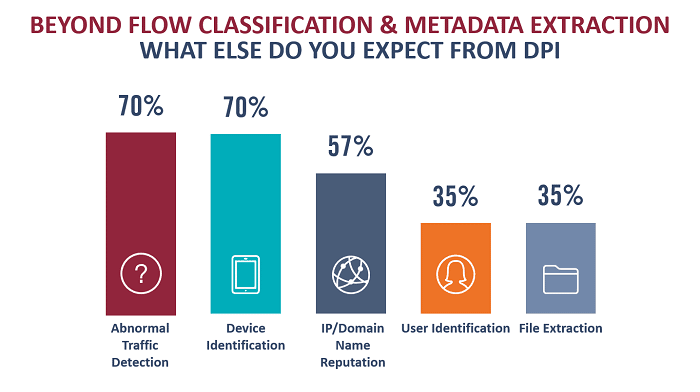
The following are a few key insights from the survey:
- Threat Detection: The elimination of conventional network borders – and with them perimeter control points – makes traffic-based threat detection more important. Abnormal traffic detection was identified as a top use case for DPI software.
- Device Identification: 70 percent of respondents require classification of connected devices in enterprise and IoT/industrial networks.
- Encryption: The increased use of encryption along with adoption of the stringent TLS 1.3 security protocol (mandatory in 5G), threatens essential traffic visibility for many vendors.
- SASE: Most vendors report that they have or are developing cloud solutions, with half of them planning to offer a Secure Access Service Edge (SASE) solution, which integrates security and networking in a cloud-based service.
To see all the survey results and the trends the responses reveal, download The Future of DPI report (PDF file).
For a presentation and panel discussion of the survey results, see the on-demand webinar.
* The survey was conducted among product managers working for the following types of solution vendors:
- Telecommunications: Software Defined Networking (SD WAN, SASE, NFV), Network Performance Management, Subscriber Experience Management, Revenue Assurance & Fraud Management
- Enterprise Networking: Cloud Networking (SD WAN/SASE), Network Performance Management, Operations Intelligence & Automation
- Cybersecurity: Network Security (NG Firewalls, Cyber Threat Hunting), Cloud/WAN Security (SD WAN/SASE, Web Gateways, Web Application Firewalls, …), Security Platforms (SIEM, Security Operations Automation & Orchestration, …), Cyber Defense (Crime Fighting, Cyber Intelligence, …)