Today we announced the release of our new product SIGIL. Short for SIGnalling Intelligence Layer, SIGIL is a cloud-based service that analyses the outputs from telecom signalling firewalls around the world. By applying a series of algorithms to this activity, SIGIL is able to provide intelligence about both Global and local attacks to any signed up mobile operator. In short it allows operators to really understand the risk of SS7 attacks in their network. Furthermore, it also allows them to reduce that risk by leveraging advanced research on attacks that have been seen elsewhere to greatly improve their defences.
The origin of this idea came from a series of events we encountered last year. In this period, what we call the ‘Central Asian Scanning event’ occurred, where multiple customer operators worldwide received a burst of suspicious SS7 activity from SS7 addresses in Central Asia. If you were to examine the activity in each operator in isolation it would not be so interesting in itself. However when we combined the information and research we could see a much more complex picture of probing defences for use in advanced attacks. Once we recognised the seriousness of this attacker, we classified this as a high-threat ‘Attack Platform’ and rigorously monitored it carefully in multiple customer operators, ensuring that it wasn’t successful.
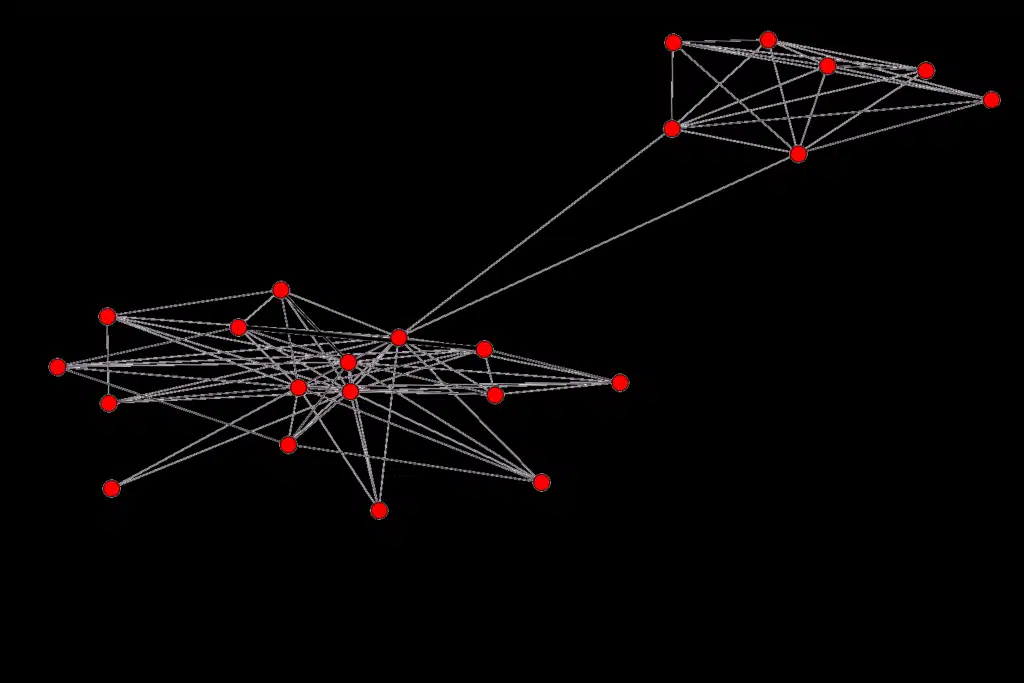
SIGIL visualization of mTAN interception platform
Unfortunately, this attacker is also the best known public example of malicious SS7 attacks, as it is the source of the successful banking mTAN interception attacks in Germany reported a few months ago. While we cannot go into too much details as this criminal group is under legal investigation (which we are assisting), for us this was a graphic illustration of the benefits of collaborative intelligence and research. A single operator investigating this would have struggled to determine the true risk behind this until it was too late, especially as it tries to stealthily bypass defences and may not be noticed. This for us was the impetus to build SIGIL, as it tackles 3 key areas that operators need assistance with in the field of SS7 Security – Understanding, Defending and Predicting.
Understanding the Threat
The first is that it can be a struggle for Operators to understand what is really going on in their network. Signalling firewalls use a series of methods to detect activity that seems abnormal and report these, the volumes can vary but it can be between a few thousands to several hundred thousand events a day, depending on the size of the network. Beyond that point, Firewalls typically provide little in the way of commentary or intelligence.
We found that through our investigation and research we could start to separate out the ‘noise’ events from really malicious attacks. Being able to classify and identify the different malicious activity, and combine with intelligence is really essential in any cyber-security area. If you don’t do this, security teams end up focusing on high-volume but low risk attacks, while the truly dangerous activity (normally at much lower volumes) which should be tracked carefully gets missed. To help operators we’ve built much of this research into SIGIL. In practical terms operators can know if that burst of unusual activity is as simple as a badly configured telecom node in somebody else’s network, or a criminal or state-sponsored group trying to intercept communications and subscribers need to be warned.
Defending the Network
Following closely on from understanding the ‘badness’ in an operator’s network by using SIGIL, the operator can now make much better decisions on defending against attacks and engineering defences. At a high-level this allows the operators to have more certainty on whether to block unusual SS7 activity or not.
This decision on whether to block or allow is not always apparent. Experience and knowledge in SS7 Security is not a widespread skill. Technical and network staff in Mobile Operators know their network, but knowing how attacks actually manifest, and how to look for attacks which may have evaded initial defences is different. We’ve spent a lot of time using our experience to building up algorithms that are part of SIGIL. The practical benefit of this is that staff in operators don’t have to spend the same time trying to replicate the same effort, and can focus on dealing with the attacks themselves.
Predict the Future
Finally, and possibly most useful, by using SIGIL operators can also receive a feed of information on not only attackers that they have experienced, but also about sources of attacks that they have not experienced yet, i.e. information on attackers before they can strike the network. This has obvious benefits in allowing them to block sources of malicious signalling activity ahead of time.
It also helps defend against potential future developments by determined attackers. Intriguingly, we are starting to identify and detect looser connections between these Attackers, which show that many of these Attackers may re-use the same methods and access points. Examples of this is that we have seen cases of both criminal and state-sponsored malicious users of SS7 networks, sharing similar (but not identical) techniques and access points, and these similarities are evolving. This is an area of future research but for now it means that knowing in advance the sources of complex attacks elsewhere, and not waiting for them to attack each operator, is critical
We believe that SIGIL is a critical development in the evolution of security for mobile operators, and ultimately will help all of us who use mobile phones, as these rely on the security of the SS7 network. In the seemingly never-ending Game of Phone security, SIGIL provides understanding, defence and prediction to help level the playing field.